Multiple Choice Questions and Answers on Cloud Security of Cloud Computing for Freshers
https://www.computersprofessor.com/2018/11/multiple-choice-questions-and-answers_12.html
1. Which of the following service provider provides the least amount of built in security ?
a) SaaS
b) PaaS
c) IaaS
d) All of the mentioned
Answer: c
Explanation: You get the least amount of built in security with an Infrastructure as a Service provider, and the most with a Software as a Service provider.
2. Point out the correct statement:
a) Different types of cloud computing service models provide different levels of security services
b) Adapting your on-premises systems to a cloud model requires that you determine what security mechanisms are required and mapping those to controls that exist in your chosen cloud service provider
c) Data should be transferred and stored in an encrypted format for security purpose
d) All of the mentioned
Answer: d
Explanation: When you identify missing security elements in the cloud, you can use mapping to work to close the gap.
3. Which of the following services that need to be negotiated in Service Level Agreements ?
a) Logging
b) Auditing
c) Regulatory compliance
d) All of the mentioned
Answer: d
Explanation: Logging, auditing, and regulatory compliance are all features that require planning in cloud computing systems.
4. The following flowchart is intended to evaluate __________ in any cloud.
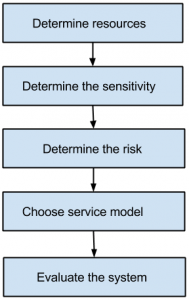
a) risk
b) errors
c) inconsistencies
d) none of the mentioned

a) risk
b) errors
c) inconsistencies
d) none of the mentioned
Answer: a
Explanation: Your risks in any cloud deployment are dependent upon the particular cloud service model chosen and the type of cloud on which you deploy your applications.
5. Point out the wrong statement:
a) You can use proxy and brokerage services to separate clients from direct access to shared cloud storage
b) Any distributed application has a much greater attack surface than an application that is closely held on a Local Area Network
c) Cloud computing don’t have vulnerabilities associated with Internet applications
d) All of the mentioned
Answer: c
Explanation: Additional vulnerabilities arise from pooled, virtualized, and outsourced resources.
6. Which of the following area of cloud computing is uniquely troublesome ?
a) Auditing
b) Data integrity
c) e-Discovery for legal compliance
d) All of the mentioned
Answer: d
Explanation: Storing data in the cloud is of particular concern.
7. Which of the following is operational domain of CSA ?
a) Scalability
b) Portability and interoperability
c) Flexibility
d) None of the mentioned
Answer: b
Explanation: CSA is an industry working group that studies security issues in cloud computing and offers recommendations to its members.
8. Which of the following is considered an essential element in cloud computing by CSA ?
a) Multi-tenancy
b) Identity and access management
c) Virtualization
d) All of the mentioned
Answer: a
Explanation: Multi-tenancy adds a number of additional security concerns to cloud computing that need to be accounted for.
9. Which of the following is used for Web performance management and load testing ?
a) VMware Hyperic
b) Webmetrics
c) Univa UD
d) Tapinsystems
Answer: b
Explanation: CA Cloud Insight is a cloud metrics measurement service.
10. Which of the following is application and infrastructure management software for hybrid multi-clouds ?
a) VMware Hyperic
b) Webmetrics
c) Univa UD
d) Tapinsystems
Answer: c
Explanation: Tapinsystems is provisioning and management service.































